1. In which situation would an ESD strike potentially cause harm to the PC?
- when replacing a mechanical hard drive with an M.2 SSD *
- when installing an additional display in a workplace cubicle
- when using a grounded mat and working on a computer on an ungrounded workbench
- when installing a dual-voltage power supply
2. A person has started a new technical job. In which situation would ESD be an issue?
- when installing a processor *
- when using a grounded mat and working on a computer on an ungrounded workbench
- when installing a dual-voltage power supply
- while exchanging one laptop AC adapter with one that is not from the original equipment manufacturer
3. A technician is about to begin preventive maintenance on a company PC. In which situation would ESD be an issue?
- when replacing a motherboard *
- while attaching speakers to a surround sound card
- when using a grounded mat and working on a computer on an ungrounded workbench
- when installing a dual-voltage power supply
4. An instructor has given a student an assignment to assemble a PC. In which situation should the student be aware that ESD is an issue?
- when installing RAM *
- when working in a corporate environment that has carpet installed under tower PCs
- when using a grounded mat and working on a computer on an ungrounded workbench
- when installing a dual-voltage power supply
5. What two motherboard components control the system boot operations? (Choose two.)
- BIOS chip *
- UEFI chip *
- Northbridge chip
- Southbridge chip
- CPU
6. A technician is upgrading an ATX motherboard with another ATX motherboard. Which component might be affected by this and need to be upgraded and bought as an additional purchase?
- BIOS
- chipset
- CMOS battery
- CPU *
- PCIe adapter
7. A customer has requested that a PC be built that will support eSATA. Which component should be checked to be sure that this feature is supported?
- CPU
- chipset *
- hard disk
- RAM module
8. Which memory module used to hold instructions for booting a PC and loading the OS, but is still used on adapters even though the memory contents cannot be changed?
- RAM
- ROM *
- cache
- main memory
9. What is a characteristic of DDR SDRAM?
- It transfers data twice per clock cycle compared to once per clock cycle for SDRAM. *
- DDR SDRAM modules have double the number of pins of SDRAM memory modules.
- It is dynamic memory whereas SDRAM is static memory.
- It operates at double the voltage of SDRAM memory.
10. What are two safety hazards when dealing with laser printers? (Choose two.)
- high voltage *
- hot components *
- heavy metals
- proprietary power bricks
- unwieldy card cages
11. Which component requires a technician to install screws externally through the PC case?
- RAM
- CPU
- motherboard
- power supply *
12. A technician is installing an internal HDD. To which motherboard connector will the technician connect the data cable?
- ATX
- PCI
- PWR_SW
- SATA *
13. Refer to the exhibit. A technician has been asked to install a video card. Which section of the motherboard will the technician use to install the card?
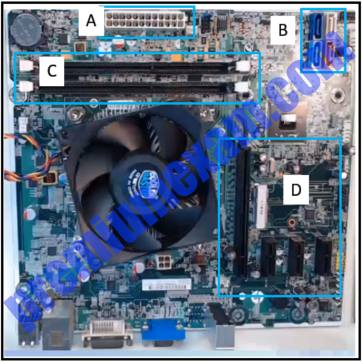

- section A
- section B
- section C
- section D *
14. When a PC is being assembled, what component is connected to the motherboard with a SATA cable?
- the optical drive *
- the network interface card
- the video card
- the power supply
15. A technician is troubleshooting a computer that is experiencing hardware failure detected by the BIOS. What is one way this failure is indicated?
- The computer automatically boots into Safe Mode and displays a warning on the screen.
- The screen flashes with a red background and displays a warning message.
- The computer emits a pattern of beeps indicating the failing device. *
- The computer returns an error message that indicates the I/O address of the failing device.
16. Which three features can be configured in the BIOS settings to secure a computer? (Choose three.)
- MAC filtering
- drive encryption *
- TPM *
- file encryption
- TKIP key
- passwords *
17. What is the purpose of RAID adapters?
- to allow older PCI technology expansion slots to be used
- to provide enhanced audio and graphic capabilities
- to connect multiple storage devices for redundancy or speed *
- to connect peripheral devices to a PC to improve performance
18. When a new motherboard is being installed, between which two components must thermal compound be applied? (Choose two.)
- CPU *
- RAM
- chassis
- heat sink *
- chipset
- motherboard
19. What is the purpose of a Safety Data Sheet?
- to specify procedures for dealing with potentially hazardous materials *
- to specify procedures in designing and building common computer systems
- to specify procedures for the operation of sensitive components and prevention of electrostatic discharge
- to specify procedures in the use of humidity control and prevention of moisture damage
20. Which negative environmental factor does cleaning the inside of a computer reduce?
- dust *
- EMI
- rust
- ESD
21. What is a recommended procedure to follow when cleaning computer components?
- Remove the CPU before cleaning.
- Blow compressed air on cooling fans so that they will spin when dust is being removed.
- Use window cleaner on LCD screens.
- Hold cans of compressed air upright while spraying. *
22. On the production floor, a furniture plant has laptops for process monitoring and reporting. The production floor environment is around 80 degrees Fahrenheit (27 degrees Celsius). The humidity level is fairly high around 70 percent. Fans are mounted in the ceiling for air circulation. Wood dust is prevalent. Which condition is most likely to adversely affect a laptop that is used in this environment?
- the temperature
- the humidity
- the air flow
- the dust *
23. After a technician tests a theory of probable causes, what two actions should the technician take if the testing did not identify an exact cause? (Choose two.)
- Establish a new theory of probable causes. *
- Randomly replace components one at a time until the problem is solved.
- Document each test tried that did not correct the problem. *
- Verify full system functionality.
- Test all remaining possible causes starting with the most complex.
24. What would happen if a PC that contains a power supply that does not automatically adjust for input voltage is set to 230 volts and attaches to an outlet in the United States?
- The power supply would explode.
- The PC would not turn on. *
- The PC would display an error code.
- The PC would emit a series of beeps.
25. Which type of network spans a single building or campus and provides services and applications to people within a common organizational structure?
- PAN
- WAN
- LAN *
- MAN
26. What are two types of wired high-speed Internet connections? (Choose two.)
- cable *
- satellite
- cellular
- DSL *
- dial-up
27. In what two situations would UDP be better than TCP as the preferred transport protocol? (Choose two.)
- when applications need to guarantee that a packet arrives intact, in sequence, and unduplicated
- when a faster delivery mechanism is needed *
- when delivery overhead is not an issue
- when applications do not need to guarantee delivery of the data *
- when destination port numbers are dynamic
28. The current IP configuration of a small company is done manually and is time-consuming. Because of increased network growth, a technician needs a simpler way for IP configuration of workstations. Which service would simplify the workstation IP configuration task?
- APIPA
- DHCP *
- DNS
- ICMP
29. A company is looking for a next-generation firewall that provides VPN functionality, IDS/IPS functionality, and DoS/DDoS protection. Which device would be best suited for this task?
- multipurpose device
- router
- endpoint management server
- UTM *
- TPM
30. A student is helping a friend with a home computer that can no longer access the Internet. Upon investigation, the student discovers that the computer has been assigned the IP address 169.254.100.88. What could cause a computer to get such an IP address?
- static IP addressing with incomplete information
- interference from surrounding devices
- reduced computer power supply output
- unreachable DHCP server *
31. What three values must be added to the IPv4 properties of a NIC in order for a computer to have basic connectivity with the network? (Choose three.)
- subnet mask *
- DHCP server address
- domain name
- default gateway *
- speed and duplex
- IP address *
32. A device has an IPv6 address of 2001:0DB8:75a3:0214:0607:1234:aa10:ba01 /64. What is the host identifier of the device?
- 2001:0DB8:75a3
- 0607:1234:aa10:ba01 *
- 2001:0DB8
- ba01
33. How can a user prevent specific applications from accessing a Windows computer over a network?
- Enable MAC address filtering.
- Disable automatic IP address assignment.
- Block specific TCP or UDP ports in Windows Firewall. *
- Change default usernames and passwords.
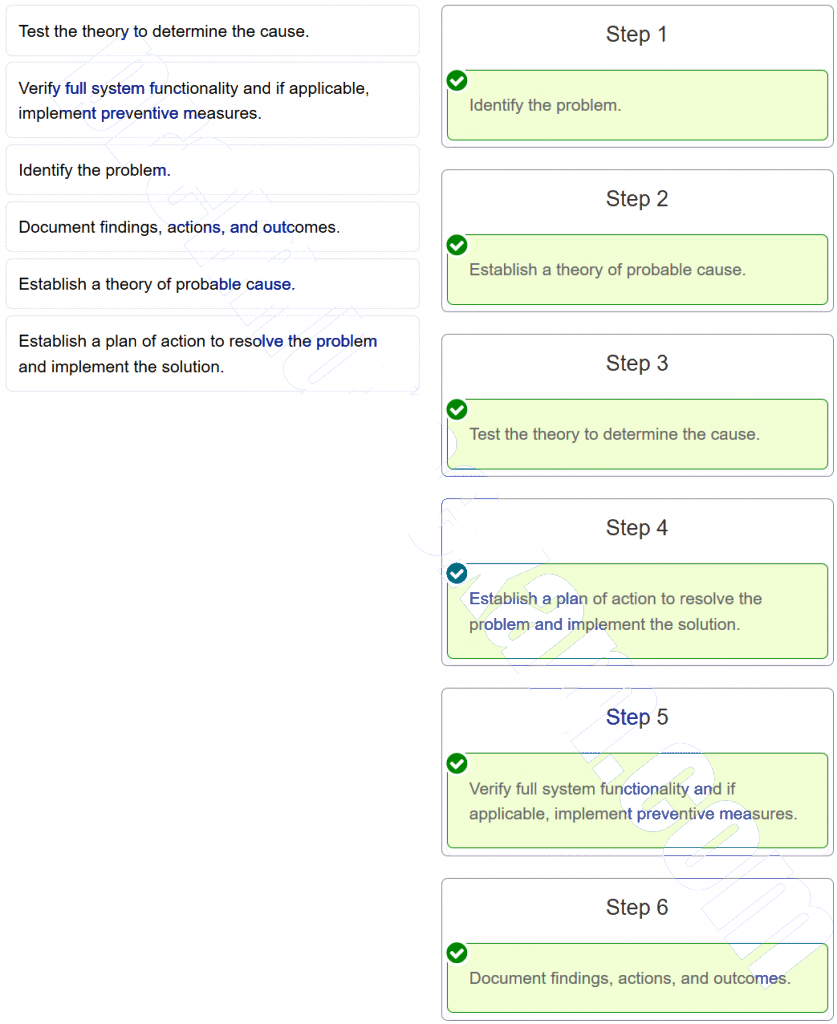
34. Place the six stages of the troubleshooting process in the correct order.

35. A technician has been asked to configure Wi-Fi calling on a corporate mobile device. In which situation would this feature be most advantageous?
- in an emergency situation and no minutes are left on the phone
- when sending WEA updates
- when in an area with poor cellular coverage *
- in a store transaction making a payment using the mobile device
36. Which statement is true about laptops?
- Most of the internal components that are designed for laptops cannot be used for desktops. *
- Laptop motherboards have standard form factors.
- Laptops use fewer components than desktops use.
- Laptop CPUs do not use cooling devices.
37. Which standard provides a bridge between laptop hardware and the operating system and a way for technicians to configure power management schemes to get the best performance?
- ACPI *
- PCIe
- Bluetooth
- 802.11
38. Which two laptop components are considered replaceable by the customer. (Choose two.)
- battery *
- integrated card reader
- mini-PCIe module
- RAM *
- display
39. A user wants to synchronize some apps, movies, music, and ebooks between mobile devices. What are the two types of connections used to synchronize this type of data? (Choose two.)
- cellular
- Wi-Fi *
- USB *
- Bluetooth
- NFC
40. A technician is explaining the differences between inkjet printers and laser printers to a customer. Which two comparisons should the technician make? (Choose two.)
- Inkjet printers are less expensive as an initial purchase than laser printers. *
- A laser printer is significantly slower than an inkjet printer.
- Both laser and inkjet printers produce poor quality images.
- The laser printer output is dry after printing, but an inkjet printer may still have wet ink on the paper after printing. *
- Inkjet printers use plain paper to make economical prints, but laser printers require more expensive thermal paper.
41. A user chooses the collate option and prints two copies of a three-page document. What is the order in which the pages are printed?
- pages 1, 1, 2, 2, 3, 3
- pages 1, 2, 3, 1, 2, 3 *
- pages 3, 3, 2, 2, 1, 1
- pages 3, 2, 1, 3, 2, 1
42. A color laser printer is used to print documents with graphics and photographs. Users are complaining that printing takes too long. Which component of the printer should be upgraded in order to improve printing performance?
- CPU
- RAM *
- hard drive
- toner cartridges
43. What service is available for Windows to provide software print server services to MAC OS clients?
- Bonjour Print Server *
- Print to XPS
- Apple AirPort Extreme
- Apple AirPrint
44. Which three components are typically found in laser printer maintenance kits? (Choose three.)
- fuser assembly *
- primary corona
- pickup rollers *
- transfer rollers *
- secondary corona
- paper trays
45. A technician is installing a new printer in a cool, damp environment. After the printer cabling is done, and the software and print driver are installed, the printer test page jams. What is the most likely cause of the print failure?
- incorrect printer driver
- too much humidity *
- not enough printer memory
- loose printer cables
46. A data center has recently updated a physical server to host multiple operating systems on a single CPU. The data center can now provide each customer with a separate web server without having to allocate an actual discrete server for each customer. What is the networking trend that is being implemented by the data center in this situation?
- BYOD
- virtualization *
- maintaining communication integrity
- online collaboration
47. How does virtualization help with disaster recovery within a data center?
- Power is always provided.
- Less energy is consumed.
- Server provisioning is faster.
- Hardware does not have to be identical. *
48. Which two hypervisors are suitable to support virtual machines in a data center? (Choose two.)
- Virtual PC
- VMware Fusion
- VMware ESX/ESXi *
- Oracle VM VirtualBox
- Microsoft Hyper-V 2012 *
49. A web designer accesses a company Windows 10 computer remotely. The designer often needs to simultaneously open multiple applications, such as a web page editor and a graphics editor. Rather than opening them in multiple windows, the designer opens them in different virtual desktops. What technology is being used by the designer?
- virtual reality
- Windows Virtual Desktop *
- cloud-based applications
- virtual desktop infrastructure
50. Which Cloud computing service would be best for an organization that needs to collaboratively create applications and deliver them over the web?
- PaaS *
- IaaS
- SaaS
- ITaaS
51. Which statement describes a feature of SDRAM?
- It requires constant power to function.
- Its connector always has 240 pins.
- It can process overlapping instructions in parallel. *
- It is able to support two writes and two reads per CPU clock cycle.
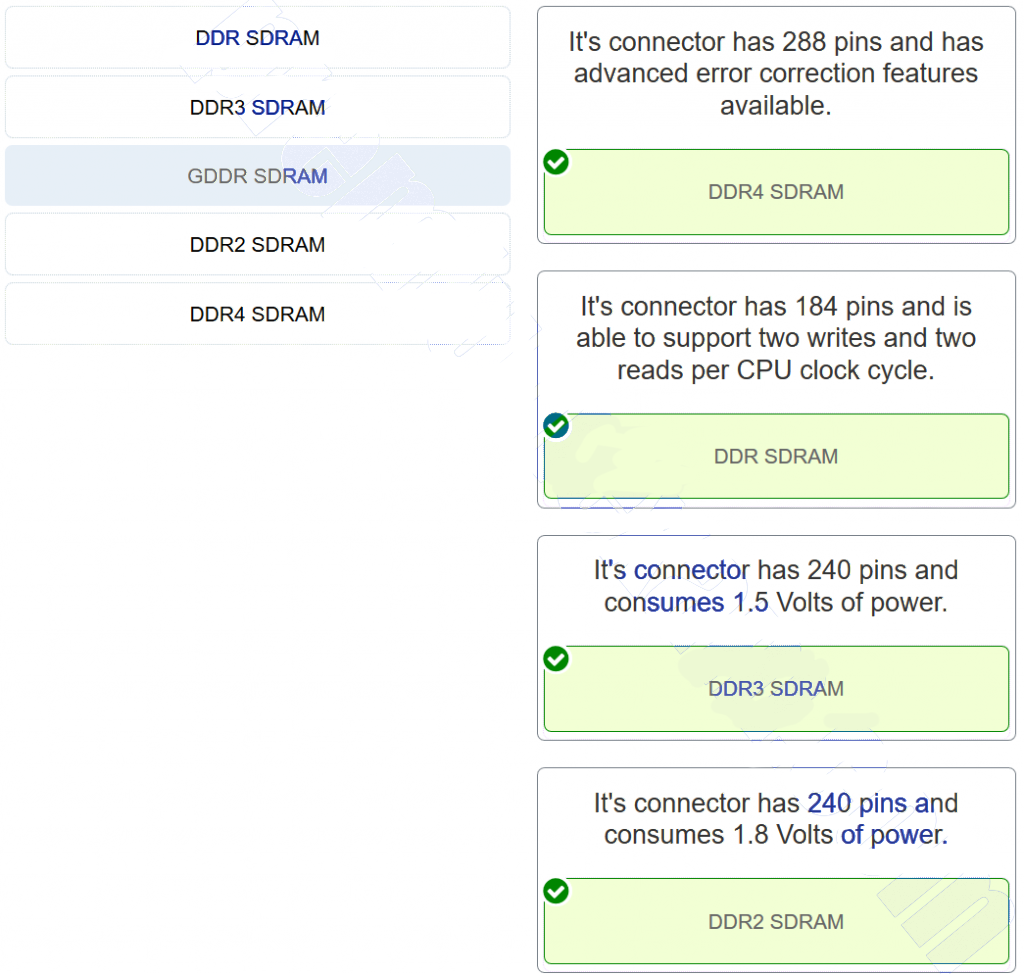
52. Match the memory type to the feature. (Not all options are used.)

53. A technician is troubleshooting a server that displays the error message “RAID not found” after a power outage over the weekend. What is a possible cause for this?
- The BIOS firmware needs updating.
- The FSB settings have changed and are wrong.
- The external RAID controller is not receiving power. *
- The CPU multiplier is set too high.
54. A customer brings in a laptop with a touch screen that is not working correctly. The touch screen either does not respond at all or provides unusual or inaccurate responses. What is a possible cause for such behavior?
- The battery is not seated properly.
- The DC jack is not grounded or is loose.
- The digitizer is faulty.
- Too many apps are open. *
55. What are two security risks associated with sharing printers in a corporate environment? (Choose two.)
- user authentication *
- cached files *
- document viewing in the print queue
- dumpster diving
- shoulder surfing
56. Which change management process component is concerned with the business processes that are affected by changes?
- assessment *
- approval
- implementation
- identification
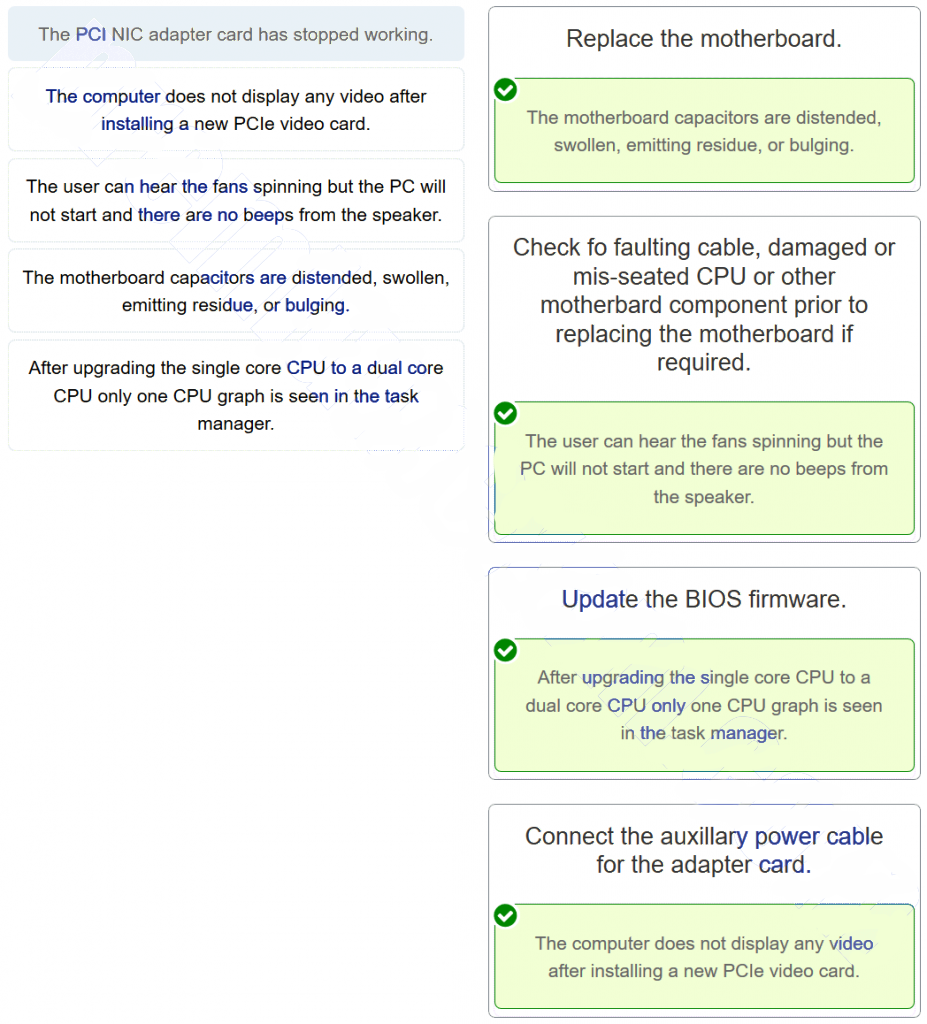
57. Match the problem to the possible solution. (Not all options are used.)

58. A computer technician is installing a RAID. If the RAID uses mirroring and striping, which RAID level is the technician using?
- 10
- 5
- 1
- 8
59. A computer technician is installing a RAID. If the RAID uses mirroring, which RAID level is the technician using?
- 1
- 6
- 5
- 3
60. A computer technician is installing a RAID. If the RAID uses striping with parity, which RAID level is the technician using?
- 5
- 6
- 1
- 4
61. A computer technician is installing a RAID. If the RAID uses striping, which RAID level is the technician using?
- 0 *
- 6
- 5
- 2
62. A computer technician is installing a RAID. If the RAID uses striping with double parity, which RAID level is the technician using?
- 6 *
- 1
- 5
- 7
63. A technician is upgrading many PCs used within the company. How should the technician dispose of an old battery?
- Recycle following local regulations. *
- Throw it away.
- Take it to the garbage dump.
- Burn it.
64. A technician is upgrading many PCs used within the company. How should the technician dispose of a broken monitor?
- Recycle following local regulations. *
- Bury it.
- Take it to the garbage dump.
- Burn it.
65. A technician is upgrading many PCs used within the company. How should the technician dispose of an old power supply?
- Recycle following local regulations. *
- Burn it.
- Take it to the garbage dump.
- Bury it.
66. A technician is upgrading many PCs used within the company. How should the technician dispose of old RAM?
- Recycle following local regulations. *
- Destroy it with a hammer.
- Burn it.
- Bury it.
67. A technician is upgrading many PCs used within the company. How should the technician dispose of an old motherboard?
- Recycle following local regulations. *
- Seal in a plastic bag before putting in the garbage.
- Give it to your neighbor.
- Destroy it with a hammer.
68. A technician is upgrading many PCs used within the company. How should the technician dispose of an old hard drive?
- Recycle following local regulations. *
- Seal in a cardboard box.
- Give it to your neighbor.
- Destroy it with a hammer.
69. After continuous morning use, a computer suddenly reboots without the intervention of the user. What are the two most likely hardware parts that could cause this problem? (Choose two.)
- CPU *
- power supply *
- hard drive
- RAID
- BIOS
- wireless NIC
70. A technician has been called in to investigate a problem with the computer rebooting randomly throughout the day. What two pieces of hardware could cause this problem? (Choose two.)
- CPU *
- power supply *
- surge strip
- ROM
- wireless NIC
- motherboard
71. For two days in a row, a user has noticed that the computer reboots several times before it eventually starts. What are two suspect components? (Choose two.)
- CPU *
- power supply *
- BIOS
- ROM
- wireless NIC
- motherboard
72. While a user is working on a spreadsheet, the computer reboots. What are two components that could cause this issue? (Choose two.)
- CPU *
- power supply *
- ROM
- BIOS
- RAID
- wireless NIC
73. A client packet is received by a server. The packet has a destination port number of 137. What service application is the client requesting?
- NetBIOS (NetBT) *
- SMB/CIFS
- HTTPS
- SLP
74. A client packet is received by a server. The packet has a destination port number of 22. What service application is the client requesting?
- SSH *
- SMB/CIFS
- HTTPS
- SLP
75. A client packet is received by a server. The packet has a destination port number of 143. What service application is the client requesting?
- IMAP *
- SMB/CIFS
- HTTPS
- SLP
76. A client packet is received by a server. The packet has a destination port number of 23. What service application is the client requesting?
- Telnet *
- SMB/CIFS
- HTTPS
- SLP
77. A client packet is received by a server. The packet has a destination port number of 161. What service application is the client requesting?
- SNMP *
- SMB/CIFS
- HTTPS
- SLP
78. A client packet is received by a server. The packet has a destination port number of 389. What service application is the client requesting?
- LDAP *
- SMB/CIFS
- HTTPS
- SLP
79. A client packet is received by a server. The packet has a destination port number of 25. What service application is the client requesting?
- SMTP *
- SMB/CIFS
- HTTPS
- SLP
80. A client packet is received by a server. The packet has a destination port number of 427. What service application is the client requesting?
- SLP *
- SMB/CIFS
- SMTP
- DNS
81. A client packet is received by a server. The packet has a destination port number of 53. What service application is the client requesting?
- DNS *
- SMTP
- DHCP
- TFTP
82. Which is the compressed format of the IPv6 address 2001:0db8:0000:0000:0000:a0b0:0008:0001?
- 2001:db8::a0b0:8:1
- 2001:db80:0:1::80:1
- 2001:db8::ab8:1:0:1000
- 2001:db80:::1::80:1
83. Which is the compressed format of the IPv6 address fe80:09ea:0000:2200:0000:0000:0fe0:0290?
- fe80:9ea:0:2200::fe0:290
- fe80:9:20::b000:290
- fe80:9ea0::2020:0:bf:e0:9290
- fe80:9ea0::2020::bf:e0:9290
84. Which is the compressed format of the IPv6 address 2002:0042:0010:c400:0000:0000:0000:0909?
- 2002:42:10:c400::909 *
- 200:420:110:c4b::910:0:90
- 2002:4200::25:1090:0:99
- 2002:42::25:1090:0:99
85. Which is the compressed format of the IPv6 address 2002:0420:00c4:1008:0025:0190:0000:0990?
- 2002:420:c4:1008:25:190::990 *
- 2002:4200::25:1090:0:99
- 2002:42:10:c400::909
- 2002:42::25:1090:0:99
86. Which is the compressed format of the IPv6 address 2001:0db8:0000:0000:0ab8:0001:0000:1000?
- 2001:db8::ab8:1:0:1000 *
- 2001:db8::a0b0:8:1
- 2001:db8:1::ab8:0:1
- 2001:db8:0:1::8:1
87. Which is the compressed format of the IPv6 address fe80:0000:0000:0000:0220:0b3f:f0e0:0029?
- fe80::220:b3f:f0e0:29 *
- fe80:9ea0::2020:0:bf:e0:9290
- fe80:9ea:0:2200::fe0:290
- fe80:9ea0::2020::bf:e0:9290
88. Which is the compressed format of the IPv6 address fe80:9ea0:0000:2020:0000:00bf:00e0:9290?
- fe80:9ea0::2020:0:bf:e0:9290 *
- fe80:9:20::b000:290
- fe80:9ea:0:2200::fe0:290
- fe80::0220:0b3f:f0e0:0029
89. What ACPI power state describes when the CPU and RAM are off and the contents of RAM have been saved to a temporary file on the hard drive?
- S4 *
- S1
- S2
- S3
90. What ACPI power state describes when the CPU and RAM are still receiving power but unused devices are powered down?
- S1 *
- S2
- S3
- S4
91. What ACPI power state describes when the CPU is off, but the RAM is refreshed?
- S2 *
- S1
- S3
- S4
92. What ACPI power state describes when the computer is off?
- S5 *
- S1
- S2
- S3
93. What ACPI power state describes when the CPU is off and the RAM is set to a slow refresh rate, often called suspend mode?
- S3 *
- S4
- S2
- S5
94. What ACPI power state describes when the computer is on and the CPU is running?
- S0 *
- S4
- S3
- S5
95. A reporter is trying to print several high resolution photographs but the color laser printer is going extremely slowly. What should the technician do to resolve the issue?
- Add more RAM to the printer. *
- Rewind the ribbon.
- Connect the printer using wireless.
- Install a USB hub.
- Update the BIOS.
96. A new printer has just been installed deep in a mine. When test pages are printed, the paper constantly jams. What should the technician do to resolve the issue?
- Move the printer to a less-humid location. *
- Clean the printer.
- Connect the printer using wireless.
- Install a USB hub.
- Update the BIOS.
97. A user complains that recently every printed document has vertical lines and streaks on the paper. What should the technician do to resolve the issue?
- Distribute the toner more evenly within the cartridge. *
- Clean the printer.
- Connect the printer using wireless.
- Install a USB hub.
- Update the BIOS.
98. A school is installing a new shared printer but the printer is not showing up on the list of available printers. What should the technician do to resolve the issue?
- Manually add the printer IP address. *
- Reset the page counter.
- Connect the printer using wireless.
- Install a USB hub.
- Update the BIOS.
99. Employees are complaining that they send print jobs to a newly installed printer but the print jobs never print. What should the technician do to resolve the issue?
- The printer is connected to the wrong port. Modify the port. *
- Check the vibration of the crystals.
- Connect the printer using wireless.
- Install a USB hub.
- Update the BIOS.
100. Users have noticed that the colors on their printed documents are different from the colors that they see on their computer screens. What should the technician do to resolve the issue?
- Calibrate the printer. *
- Install a USB hub.
- Reset the page counter.
- Check the vibration of the crystals.
- Connect the printer using wireless.
101. A technician has just completed a preventive maintenance on the department printer. Users are now complaining that the printer is no longer available. What should the technician do to resolve the issue?
- Check that the printer is plugged into a power source. *
- Connect the printer using wireless.
- Reset the page counter.
- Check the vibration of the crystals.
- Install a USB hub.
102. Employees of a small business are complaining that the printer is printing faded images. What should the technician do to resolve the issue?
- Replace the toner cartridge. *
- Update the BIOS.
- Reset the page counter.
- Check the vibration of the crystals.
- Install a USB hub.
103. A photographer is complaining about the following printer issue: The printer issues a “Document failed to print” message. What are two possible causes of this issue? (Choose two.)
- A cable is loose or disconnected. *
- The printer is no longer shared. *
- The paper tray is flimsy.
- The laser printer is emitting too much radiation.
- The wrong printer type has been selected.
104. A reporter is complaining about the following printer issue: The printer is printing unknown characters. What are two possible causes of this issue? (Choose two.)
- The wrong or an outdated printer driver is installed. *
- The printer has a loose connection. *
- The laser printer is emitting too much radiation.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
105. A manager is complaining about the following printer issue: The printer is printing incorrect colors. What are two possible causes of this issue? (Choose two.)
- The print heads might need to be cleaned and calibrated. *
- An incorrect cartridge could be installed. *
- The printer is using the wrong cable.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
106. A technician is complaining about the following printer issue: The print appears faded on the paper. What are two possible causes of this issue? (Choose two.)
- The toner cartridge is low. *
- The paper might be incompatible with the printer. *
- The wrong printer type has been selected.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
107. A librarian is complaining about the following printer issue: The printer control panel displays no image. What are two possible causes of this issue? (Choose two.)
- The contrast of the screen may be set too low. *
- The printer is not turned on. *
- The room temperature is above normal.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
108. A teacher is complaining about the following printer issue: The paper is creased after printing. What are two possible causes of this issue? (Choose two.)
- The paper-feed tray might not be firmly adjusted against the edges of the printer. *
- The paper might be loaded incorrectly. *
- Print jobs are being sent to the wrong printer.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
109. A receptionist is complaining about the following printer issue: My impact printer produces faded or light characters. What are two possible causes of this issue? (Choose two.)
- The ribbon may be worn out. *
- The ribbon may be damaged. *
- The print queue is overloaded.
- The printer has been installed on the wrong port.
- The paper tray is flimsy.
110. A photographer is complaining about the following printer issue: The paper is not being fed into the printer. What are two possible causes of this issue? (Choose two.)
- The paper may be wrinkled. *
- The printer could be set to print to a different paper size than is currently loaded. *
- The paper tray is flimsy.
- The printer has been installed on the wrong port.
- The printer service is stopped or not working properly.
111. A laptop has an NVMe drive (C:) and a mechanical hard drive (D:). When the user tries to save a spreadsheet to the D: drive, the user notices that the D: drive is not there. What should the technician do to see if the drive is recognized by the operating system?
- Use the Disk Management Control Panel. *
- Use the Msconfig utility.
- Boot into UEFI/BIOS and see if the drive appears.
- Remove the drive and attach it to the SATA port used by the SSD. Reboot the computer and see if the drive is recognized.
112. A computer has two mechanical hard drives. The second drive (D:) is used for data storage. When trying to save an email attachment to the local hard drive, the user notices that the D: drive is not an option. What should the technician do to see if the drive is recognized by the operating system?
- Use File Explorer. *
- Swap the data cables of the mechanical drive and the SSD.
- Open a web browser and type the following: http://127.0.0.1. Verify if both drives appear in the list.
- Bring up a command prompt and type ipconfig.
113. A user reports that a drive is no longer there. The technician asks the user to demonstrate the problem. Within the application, the user demonstrates that the drive, that was present in the save options yesterday, is now no longer an option. What should the technician do to see if the drive is recognized by the operating system?
- Use Device Manager. *
- Check the Startup folder.
- Bring up a command prompt and type ipconfig.
- Swap the data cables of the mechanical drive and the SSD.
114. A computer has an SSD for the operating system and applications and uses another mechanical hard drive for data storage. The user reports that data can no longer be saved to the mechanical hard drive. What should the technician do to see if the drive is recognized by the operating system?
- Use File Explorer. *
- Swap the data cables of the mechanical drive and the SSD.
- Open a web browser and type the following: http://127.0.0.1. Verify if both drives appear in the list.
- Bring up a command prompt and type ipconfig.
115. A technician is working on a laptop and the GPS is not functioning. What is a probable cause for this situation?
- A service is disabled. *
- The GPU is overheating.
- The screen resolution needs recalibration.
- The screen refresh rate is too low.
116. A technician is working on a laptop and an app is not loading. What is a probable cause for this situation?
- An app needs to be restarted. *
- More than one app is open simultaneously.
- The screen resolution needs recalibration.
- The screen refresh rate is too low.
117. A technician is working on a laptop and an app is not responding. What is a probable cause for this situation?
- An app needs to be restarted. *
- The battery is low.
- The GPU is overheating.
- Wi-Fi is turned off.
118. A technician is working on a laptop and an error message about decryption appears when opening an email. What is a probable cause for this situation?
- A digital certificate is missing. *
- The display setting is incorrect.
- The GPU is overheating.
- Wi-Fi is turned off.
IT Essentials v6.0:
2. Which type of interface should a customer choose if connecting a single cable from a Microsoft Windows computer to output both audio and video to a high definition television?
- DVI
- HDMI*
- PS/2
- DB-15
3. Which type of input device can identify users based on their voice?
- digitizer
- KVM
- switchbiometric identification device*
- scanner
4. What type of external storage should be used by a technician to back up over 2 TB of music and video data files?
- CompactFlash card
- external flash drive
- external hard drive*
- Secure Digital card
5. What type of device provides power to a computer and allows it to be safely shut down in the event of a power loss?
- surge suppressor
- uninterruptible power supply*
- standby power supply
- power inverter
6. Which measure can help control RFI effects on wireless networks?
- Ensure the humidity and temperature levels are set as low as possible.
- Ensure the number of wireless NICs exceeds the number of wireless phones.
- Ensure the wireless network is on a different frequency than the offending source.*
- Ensure each wireless NIC is configured to operate at different frequencies from all other wireless NICs.
8. What can be tested with a digital multimeter?
- wireless signal strength and access point positioning
- basic functionality of computer ports
- copper cable location
- quality of electricity in computer components*
9. When should a technician avoid wearing an antistatic wrist strap?
- when installing RAM
- when replacing a power supply unit*
- when installing a hard drive
- when opening a computer case
10. Which solution should be used to clean a CPU and a heat sink?
- soap and water
- rubbing alcohol
- a diluted ammonia solution
- isopropyl alcohol
11. Which two types of expansion slots would be used by a wireless NIC in a computer today? (Choose two.)
- PCIe*
- AGP
- PCI*
- DIMM
- ISA
15. What is the most important reason for a company to ensure that computer preventive maintenance is done?
- Preventive maintenance provides an opportunity for junior technicians to obtain more experience in a non-threatening or problem environment.
- Preventive maintenance helps to protect the computer equipment against future problems.*
- Preventive maintenance allows the IT department to regularly monitor the contents of user hard drives to ensure computer use policies are being followed.
- Preventive maintenance enables the IT manager to check on the location and state of the computer assets.
16. A technician opens up a PC to work on it, and finds that it is very dusty inside. What should the technician do?
- Ignore the dust, as it does not affect the computer.
- Use a lint-free cloth sprayed with a cleaning solution to remove excess dust.
- Use a can of compressed air to remove excess dust.*
- Use a moistened cotton swab to remove excess dust.
17. Which built-in tool is available on a Mac OS X machine to perform disk backups?
- Disk Utility
- Deja Dup
- Finder
- Time Machine*
18. A computer technician performed a number of actions to correct a problem. Some actions did not solve the problem, but eventually a solution was found. What should be documented?
- everything that was done to try to solve the problem*
- only the solution, because this solved the problem
- only the failed attempts, so that future technicians will know what not to try
- a description of the problem and solution
19. After a computer is powered on, Windows 7 fails to start. What initial procedure would a technician use to deal with this failure?
- Create a System Repair Disc and restore the image.
- Press the F12 key during the boot process and start the computer in Safe Mode.
- Boot from a Windows 7 installation media and access the System Restore utility.*
- Access the Control Panel and choose Restore Files from Backup from the System and Security menu.
20. What are two advantages of the NTFS file system compared with FAT32? (Choose two.)
- NTFS allows faster access to external peripherals such as a USB drive.
- NTFS supports larger files.*
- NTFS provides more security features.*
- NTFS allows faster formatting of drives.
- NTFS is easier to configure.
- NTFS allows the automatic detection of bad sectors.
21. What type of hard drive contains flash memory for caching frequently used data but stores the most of the data on a magnetic hard disk drive?
- USB flash drive
- solid-state drive
- embedded multimedia card
- solid-state hybrid disk*
22. What does %USERPROFILE% represent in the path C:Users%USERPROFILE%AppDataLocalTemp?
- the location of the Documents folder of a particular user
- an environment variable that is set by the operating system*
- a variable set by the administrator for each user of the system
- a fixed value that represents the level of access of a user to system files
23. A technician notices that an application is not responding to commands and that the computer seems to respond slowly when applications are opened. What is the best administrative tool to force the release of system resources from the unresponsive application?
- Task Manager*
- Add or Remove Programs
- Event Viewer
- System Restore
24. A technician has installed a new sound card in a PC but it is not operating correctly. Where should the technician look to investigate driver problems?
- Computer Management
- Device Manager*
- My Computer
- System Tools
25. Which technology provides a solution for PC virtualization?
- hypervisor*
- server clustering
- Terminal Services
- RAID
26. What are two consequences of setting an incorrect boot order in the system BIOS? (Choose two.)
- The computer locks up without any error messages.
- The computer displays a “BOOTMGR is missing” error after POST.*
- The computer displays an “Invalid Boot Disk” error after POST.*
- The computer continually restarts without displaying the desktop.
- The computer displays an ‘Inaccessible Boot Device’ error after POST.
27. A network administrator has finished migrating from a peer-to-peer network to a new client-server network configuration. What are two advantages of the new configuration? (Choose two.)
- The total cost of the new solution is considerably lower.
- Data is more secure in the event of hardware failures.*
- Individual users are in control of their own computers and network resources.
- Data resources and access are centrally controlled.*
- Personnel costs are lower because a dedicated network administrator is no longer necessary.
28. Which layer of the OSI model is responsible for physical addressing and the procedures used to access media?
- application
- data link*
- network
- transport
29. The current IP configuration of a medium size company with several subnets is done manually and is time-consuming. Because of increased network growth, a technician needs a simpler way for IP configuration of workstations. Which service or protocol would simplify the workstation IP configuration task?
- APIPA
- DHCP*
- DNS
- ICMP
30. Several messages sent to the network administrator are reporting that access to a secure server using HTTPS is failing. After checking recent updates to the company firewall, the administrator learns that the firewall is blocking HTTPS. Which port should be opened to solve the problem?
- 22
- 53
- 80
- 143
- 443*
31. Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.)
- nslookup cisco.com*
- net cisco.com
- ping cisco.com*
- nbtstat cisco.com
- ipconfig /flushdns
32. Which wireless security mode supports government grade security and offers both personal and enterprise authentication?
- WEP
- WPA2*
- WPA
- LEAP
34. A network administrator occasionally asks a technician to make sure that dust does not accumulate on devices in the network equipment closets. What is the purpose of having the technician do this job?
- Dust can cause network equipment to overheat and cause problems on the network.*
- Dust increases electromagnetic interference in nearby connected cables.
- Dust can encourage insects and other pests to live in the equipment closets.
- Dust is considered a fire hazard that poses danger to personnel and equipment.
- Dust diminishes the range of wireless services.
35. A technician installed a network adapter in a computer and wants to test network connectivity. The ping command can receive responses from workstations on the same subnet but not from remote workstations. What could be causing the problem?
- The NIC driver is out of date.
- The operating system is not compatible with the remote sites.
- The TCP/IP protocol stack is not loaded.
- The default gateway is incorrect.*
36. What are three common input devices found on laptops? (Choose three.)
- touchpad*
- fingerprint reader*
- web camera*
- external monitor
- PS/2 keyboard
- AC power connector
37. A user calls the help desk to report that a mobile device exhibits very slow performance. What could cause this problem?
- The touchscreen is not calibrated.
- An app is not compatible with the device.*
- The operating system has encountered an error.
- A power-intensive app is running at the background.
38. A computer technician has decided that a problem with a laptop can be solved by repairing a hardware component. What should be done first before attempting to repair a hardware component on a laptop?
- Consult the service manual for the laptop.*
- Ask a fellow technician for advice.
- Backup the BIOS settings.
- Remove the keyboard.
39. Which closed-ended question would be appropriate for a technician to use to narrow down the possible problems on a laptop that will not power on?
- Can the laptop operate using the AC adapter?*
- Have you changed your password recently?
- What software has been installed recently?
- What were you doing when the problem occurred?
40. A technician is troubleshooting the appearance of flashing lines on a laptop screen. What are two possible causes of this distortion? (Choose two.)
- Power to the pixels has been removed.
- The display settings have been changed.
- The GPU is not cooling correctly.*
- The LCD cutoff switch is damaged.
- The display is not correctly installed.*
41. What is an indication that the battery in a mobile device could become physically hazardous and should be immediately replaced?
- if the battery only supports the system for a reduced period of time
- if there are signs of swelling*
- if the screen brightness begins to dim
- if the device feels warm to the touch
42. Refer to the exhibit. What is true of this mobile device screen?

- Tapping and holding the arrow at the bottom left will display the Home screen.
- Text messages, news, photos and other content can be displayed in the different tiles.*
- Icons and buttons are used to represent the different apps on the phone.
- Unpinning an app from this view will uninstall the app from the phone.
- Tile sizes depend on the size of the app.
43. What are two potential risks that could result from rooting or jailbreaking a mobile device? (Choose two.)
- enabling app access to the root directory*
- not properly creating or maintaining sandboxing features*
- allowing the user interface to be extensively customized
- improving device performance
- enabling features that are disabled by a cellular carrier
44. What two tasks should be done regularly to preserve the security and integrity of data and applications on mobile devices. (Choose two.)
- Execute a factory reset once a month to remove all unidentified malicious software.
- Back up user data on a regular basis.*
- Password protect iTunes or Google Play accounts.
- Use airplane mode if you are accessing the Internet at an open Wi-Fi site.
- Ensure that the operating system software and applications contain the latest updates.*
- Unmount all unused disk partitions.
45. A tire store needs to use carbon copy paper to print customer invoices so that both the store and the customer have a copy. What is the best printer solution?
- piezoelectric printer
- inkjet printer
- thermal printer
- impact printer*
46. A user on a home network wants to share a printer from a Windows 7 computer. What must the user do in order for other Windows 7 computers in the house to obtain the proper driver?
- The user must browse the Internet, then download and install the proper driver.
- The person doing the sharing must use the Additional Drivers button in order to designate how many device drivers are allowed to be downloaded.
- Nothing. Windows automatically provides the driver.*
- The person doing the sharing must use the Additional Drivers button in order to designate the driver to be used by the other Windows 7 computers.
48. What characterizes a DDoS attack?
- Many hosts participate in a coordinated attack.*
- Infected computers are called daemons.
- It is easy to identify the source of the attack.
- All hosts must be in the same geographic area.
49. What guideline should be followed when establishing a password security policy?
- Passwords should be physically stored in a convenient location.
- Passwords should contain mainly numbers for better encryption.
- The system administrator should assign passwords to the users.
- Lockout policies should be avoided in order to increase user access.
- An expiration period should be established so that passwords frequently change.*
50. What are three features provided by the TPM module? (Choose three.)
- hashed encryption of the hard drive volume
- security for user authentication information*
- support for Windows backup
- application license protection*
- storage of digital certificates*
- support for Windows Firewall
51. What is the next troubleshooting step after a theory of probable cause has been established?
- Test the theory to determine cause.*
- Identify the exact problem.
- Establish a plan of action.
- Document findings and outcomes.
52. Once a technician understands a customer complaint, it is common to ask closed-ended questions. Which question is a close-ended one?
- What happened before the error occurred?
- Is this the first time the error occurred?*
- What happened after the error occurred?
- What error messages were displayed when the error occurred?
53. What is a characteristic of the open source license of an application software?
- It requires registration instead of purchasing.
- It cannot be used for campus-wide deployment.
- It allows users to modify and share the source code.*
- It does not require purchase in order to use the software.
- It requires acknowledged completion of a professional training course prior to use.
54. Chad, a level one call center technician, receives a customer phone call. The customer has an issue that Chad does not have the knowledge to answer. The customer is irritated that Chad cannot provide immediate assistance. Which two things should Chad do next? (Choose two.)
- Document the reason the customer called and create a support ticket.*
- Inform the customer of the need to call back later.
- Escalate the customer to a level two technician.*
- Ask the customer further questions to diagnose and attempt to fix the problem.
- Place the customer on hold until the customer has time to cool down.
55. Users in an office complain that the network printer is printing vertical lines on all pages. What is a likely cause of this problem?
- The printer does not have enough memory.
- The printer has an incorrect IP address.*
- The printer toner is low.
- The printer drum is damaged.
56. A technician is troubleshooting a Windows 7 computer that displays an “Invalid Boot Disk” error message. What would be the most likely action the technician should perform to correct the issue?
- Use the System Recovery Options to select the correct active partition.*
- Scan for and remove any virus found.
- Run chkdsk /F /R to fix the hard drive file entries.
- Replace the hard drive on the computer.
57. When a user tries to run a program, a missing or corrupt DLL message is displayed. What are two possible solutions to this problem? (Choose two.)
- Reinstall the correct drivers.
- Use the msconfig command to adjust the startup settings for the program.
- Run Windows Startup Repair.
- Run sfc/scannow in Safe Mode.*
- Reinstall the program that is associated with the corrupt DLL file.*
58. What can help control the effect of RFI on a wireless LAN?
- Ensure the humidity and temperature levels are set as low as possible.
- Ensure the number of wireless NICs exceeds the number of wireless phones.
- Ensure the wireless network is on a different frequency than the offending source.*
- Ensure each wireless NIC is configured to operate at different frequencies from all other wireless NICs.
59. A technician wants to allow users to backup and restore all the files on their computers, but does not want the users to be able to make changes to the system. How should the technician give users this functionality?
- Grant the users read permissions on all files.
- Give the users administrator rights on their computers.
- Make the users members of a group called Backup Operators.*
- Check the Folder is Ready for Archiving box in the properties of each folder.
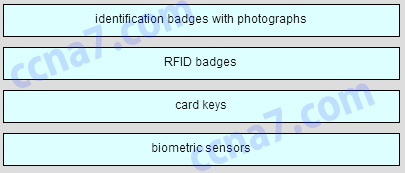
60. Match the facility access control devices to the correct descriptions. (Not all options are used.) Question
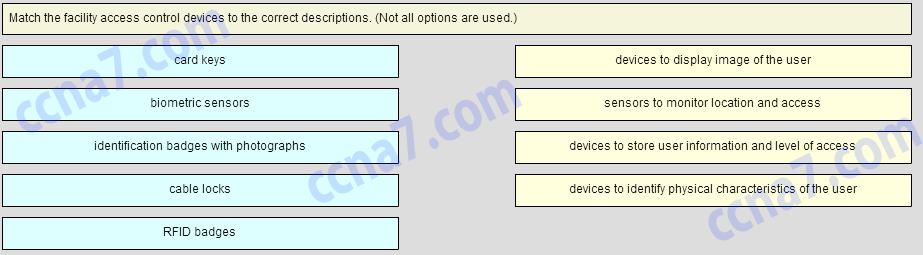
Answer
61. Why do laptop computers use CPU throttling techniques?
- to enhance the performance of the CPU
- to reduce the heat that the CPU may generate*
- to ensure the CPU is running at its peak speed
- to conserve the battery life by reducing the bus speed between the CPU and RAM
62. What tool is included in the Mac OS X for backing up disks to image files and recovering disk images?
- Disk Utility*
- Deja Dup
- Disk Error-Checking
- System Restore
63. A new technician has joined the IT team and is about to service a heavy printer. Which two precautions should be taken to avoid any injury when transporting the heavy printer to the service area? (Choose two.)
- Avoid lifting the equipment using the strength in your back.*
- Lift the equipment using the strength in your legs and knees.*
- Avoid bending your knees when lifting the printer.
- Bend your back to pick the printer up.
- Avoid lifting the printer close to your body.
64. Refer to the exhibit. As part of the process of building a computer, what is the proper order of the first three steps in the installation of a power supply?

- Steps 1, 2, 4
- Steps 1, 3, 2
- Steps 1, 4, 3*
- Steps 2, 3, 4
65. Which two operations can help prevent a mobile device from being tracked without permission? (Choose two.)
- Turn off the GPS when not in use.*
- Use a VPN connection whenever possible.
- Set the device to not store credentials.
- Set the device to connect only to known WiFi networks.
- Disable or remove apps that allow connections to the GPS.*
66. What is a characteristic of a computer power connector?
- A Molex power connector supplies power to a motherboard.
- A Molex connector and a SATA connector can be used on the same drive at the same time.
- A SATA power connector is used to connect to a hard disk drive or an optical drive.*
- An ATX main power connector supplies power to a video adapter.
67. Which expansion card can assist in troubleshooting a computer problem when no video is available?
- BIOS card
- advanced graphics card
- USB expansion card
- POST card*
68. Which two PC settings can be configured using the BIOS setup utility? (Choose two.)
- POST
- virtualization support*
- allocation of memory to applications
- enabling device drivers
- boot sequence*
69. What factor should be taken into consideration more with laptops than with desktops?
- environmental control*
- loose cables
- short circuits
- unseated adapter cards
70. What are three benefits of computer preventive maintenance? (Choose three.)
- elimination of the need for repairs
- improvement in data protection*
- extension of the life of components*
- reduction in the number of equipment failures*
- time savings for technicians making repairs
- improvement in RAM access time
71. Which step in the troubleshooting process is important to help avoid repeating repair processes that were performed previously?
- identification of the problem
- implementation of the solution
- documentation of the problem and its solution*
- preparation of a plan of action
72. A computer user complains of a computer that freezes up after about five minutes of use. The technician checks the computer BIOS to see if there might be a configuration problem that is causing the computer to behave consistently in this manner. While the technician is reviewing the information, the computer once again freezes. What is the probable cause of the computer problem?
- The BIOS is corrupt.
- The hard drive is failing.
- The CPU fan is not functioning.*
- The CMOS battery has failed.
73. Why is a full format more beneficial than a quick format when preparing for a clean OS installation?
- A full format is the only method of installing Windows 8.1 on a PC that has an operating system currently installed.
- A full format will delete files from the disk while analyzing the disk drive for errors.*
- A full format will delete every partition on the hard drive.
- A full format uses the faster FAT32 file system, whereas a quick format uses the slower NTFS file system.
74. What is the default file system used during a fresh installation of Windows 7?
- NTFS*
- HPFS
- FAT16
- FAT32
75. What is the first step an administrator should take when splitting a single partition into multiple partitions?
- Format the partition.
- Assign a drive letter to the partition.
- Extend the partition.
- Shrink the partition.*
76. A user notices that some of the programs that are installed before upgrading Windows to a new version no longer function properly after the upgrade. What can the user do to fix this problem?
- Use the System Restore utility.
- Update the driver for the graphics card.
- Run the programs in Compatibility Mode.*
- Use the recovery partition to reinstall Windows.
77. After a Windows operating system has been installed, which program would a technician use to select the programs that will run at startup?
- Ntldr
- Regedit
- Msconfig*
- Task Manager
79. What are the four layers in the TCP/IP reference model?
- application, presentation, internet, network access
- application, transport, network, data link
- application, transport, internet, network access*
- application, presentation, session, transport
- physical, data link, network, transport
80. A user wants to map a network drive on a PC that is named “WORK2” and runs Windows 7. The name of the shared resource the user wishes to map to is called “installs” and is located on a workstation called “WORK1”. What would be the correct path for mapping the network drive?
- \ usernameWORK2\installs
- \usernamepassword/WORK1/installs
- // WORK2/installs
- \work1installs*
- \usernameWork2installs
- WORK2|installs
81. A customer who travels frequently wants to know which technology is the most suitable for being connected to the corporate network at all times at low cost. Which network technology would a network administrator recommend?
- satellite
- ISDN
- cellular*
- microwave
82. What is the difference between cloud computing and a data center?
- A data center provides access to shared computing resources, wheras a cloud is a private on-premise facility that stores and processes local data.
- Cloud computing solutions are network resources and services provided to the clients through the use of services from data centers.*
- The data center makes use of more devices to process data.
- Data centers require cloud computing but cloud computing does not require data centers.
83. A user complains about being unable to connect to the wireless network. Which two actions should be part of troubleshooting the wireless connection? (Choose two.)
- Verify that the laptop is plugged into an electrical outlet.
- Reconfigure TCP/IP settings on the laptop.
- Reinsert the laptop battery.
- Try moving the laptop to different places to see if a signal can be detected.*
- Verify in the laptop software whether any wireless networks are detected. *
84. A technician installed a network adapter in a computer and wants to test network connectivity. The ping command can only receive a response from local workstations. What could be causing the problem?
- The NIC driver is out of date.
- The operating system is not compatible with the remote sites.
- The TCP/IP protocol stack is not loaded.
- The default gateway is not set.*
85. An ISP help desk technician receives a call from a customer who reports that no one at their business can reach any websites or get their e-mail. After testing the communication line and finding everything fine, the technician instructs the customer to run nslookup from the command prompt. What does the technician suspect is causing the customer’s problem?
- improper IP address configuration on the host
- hardware failure of the ISR used to connect the customer to the ISP
- bad cables or connections at the customer site
- failure of DNS to resolve names to IP addresses *
86. A technician is asked to configure the time that the system must be idle before the hard disk spins down on all the Windows-based laptops in the company. The technician configured the power options in Windows but it appears to have no effect. Where should the technician look to enable power management?
- Administrative Tools
- BIOS*
- Command Prompt
- Safe mode
- System Registry
87. A technician needs to configure a Bluetooth headset for a laptop user. Which two steps should the technician take before installing the headset? (Choose two.)
- Remove the battery.
- Disconnect AC power.
- Enable Bluetooth in BIOS Setup.*
- Ensure that the antistatic wrist strap is attached to a nonpainted portion of the laptop.
- Ensure that the laptop Bluetooth switch is enabled.*
88. What laptop component converts DC power to AC so that the display can illuminate?
- inverter*
- backlight
- CCFL
- battery
- motherboard
89. A user downloads a widget onto his Android phone but is puzzled to see that when the widget is touched an app is launched. What is a possible cause?
- The user has downloaded a virus.
- The widget is corrupt.
- The security settings of the Android OS have been compromised.
- The widget is associated with the app and this is the normal behavior.*
90. Which component uses the greatest amount of power on most mobile devices?
- LCD screen*
- camera
- CPU
- media player
91. What is the purpose of using the MIME email protocol on mobile devices?
- to enable pictures and documents to be included in email messages*
- to re-synchronize the email account with other devices
- to remotely lock the email account if the device is stolen
- to encrypt the email messages
92. What is an indication that the battery in a mobile device could become physically hazardous and should be immediately replaced?
- if the battery only supports the system for a reduced period of time
- if there are signs of swelling*
- if the screen brightness begins to dim
- if the device feels warm to the touch
94. For cleaning a laser printer, what should be used to pick up excess particles of toner?
- a HEPA-capable vacuum*
- a lint-free cloth
- isopropyl alcohol
- a damp cloth
95. Which two password control policies should an organization implement to ensure strong passwords? (Choose two.)
- Passwords should be set to expire every 60 days.*
- Passwords should contain no more than eight characters.
- Passwords must contain encrypted characters.
- Passwords should contain letters and numbers.*
- Passwords should contain only capital letters.
96. A computer technician has been asked to secure all Windows 7 computers by encrypting all the data on each computer. Which Windows feature should be used to provide this level of encryption?
- BitLocker*
- EFS
- TPM
- Windows Update
97. The activity of a previously unknown program triggers an alert by Windows firewall. What three options will the user have for dealing with this event? (Choose three.)
- Keep blocking*
- Unblock*
- Ask me later*
- Deny all
- Turn off
- Turn on
98. A technician suspects that a security issue is causing problems with a computer. What two actions could be performed to test theories of probable cause when troubleshooting the PC? (Choose two.)
- Log in as a different user.*
- Disconnect the computer from the network.*
- Search helpdesk repair logs for more information.
- Discuss solutions with the customer.
- Ask the customer open-ended questions about the problem
99. A call center technician answers a call from a frequent customer who is known to be impatient and lacks experience with computers. The customer has an issue with an application that the call center supports. The customer informs the technician that the problem had been reported before but the original technician was rude, did not listen, and did not fix the problem. If the technician is confident that the problem can be resolved by increasing the amount of memory in the computer, what should the technician do?
- Tell the customer to install 2 GB of DDR3 PC3-10600 RAM.
- Explain that the original technician is no good and the supervisor will be told.
- Suggest that the customer purchase a new computer.
- Confirm the issues and give detailed instructions to solve the problem.*
100. What expectation is defined in the service level agreement between an organization and service vendor?
- guaranteed service response time*
- maximum number of service calls per day
- chain of custody procedures
- communication etiquette rules
101. In which circumstance should a level one technician initiate an escalated work order?
- when a customer appears to be very knowledgeable
- when a customer demands talking to a particular technician
- when a problem requires expertise from another technician*
- when the technician cannot understand the problem as explained by the customer
102. An application appears frozen and is not responding to a mouse or the keyboard. What Windows OS tool can be used to stop the application?
- Event Viewer
- Task Manager*
- Device Manager
- Disk Management
103. Which two issues are likely to cause BSOD errors? (Choose two.)
- out-of-date browser
- RAM failing*
- device driver errors*
- lack of antivirus software
- power supply failure
104. A user has installed a new FTP client on a computer, but is unsuccessful in connecting to an FTP server. Which two key pieces of information should the user ensure are configured correctly on the FTP client? (Choose two.)
- username
- password
- FTP client IP address
- FTP server IP address*
- FTP client port number
- FTP server port number *
105. A technician who is working on an employee’s laptop finds that a number of files that were encrypted on a network server drive are present on the laptop drive in unencrypted form. What could cause this problem?
- Encrypted files cannot be transferred across a network.
- The new computer doesn’t have an NTFS partition.*
- The network proxy decrypted the data to scan it for malware.
- The sensitive data was transferred with the FTP protocol.
106. Users in an office complain that the network printer is printing vertical lines and streaks on all pages. What is a likely cause of this problem?
- The printer has an incorrect IP address.
- The wrong print driver is installed.
- The printer drum is damaged.*
- The printer does not have enough memory.
- Navigation Bar
EmoticonEmoticon