- 2
- 3
- 4*
- 5
- 6
2. A user has detected that one of the virtual machines in a computer is infected with a virus. Which statement about the situation is likely to be true?
- The host operating system is not necessarily infected with a virus.*
- The host machine operating system has a bug.
- All of the virtual machines running on the host are infected with a virus.
- The host machine antivirus program requires an update.
3. Which fire protection system would be best for a university computer/electronics lab?
- an overhead sprinkler system
- an electronic ion spreader
- a nonwater based fire extinguisher*
- fire suppressing hazmat blankets and supressors
4. Why should a technician avoid opening the casing of a power supply?
- Power supplies must always be replaced, not repaired.
- Hazardous levels of electricity may be present inside the power supply.*
- Power supplies are very fragile, expensive, and easy to damage.
- Only the power supply manufacturer can open the casing of a power supply.
5. What is the first step a technician should take when preparing to work on the inside of a computer?
- Remove the power supply.
- Disconnect the computer from power.*
- Disconnect the computer from the network.
- Remove external devices such as a mouse.
6. What tool can be used to find and attempt to fix file structural errors on a hard disk in Windows 7?
- Format
- Sfc
- Rd
- Chkdsk*
7. A customer asks for a solution to a printer problem that is beyond the knowledge level of the technician. What should the technician do?
- Try to fix the problem anyway.
- Tell the customer to call the printer manufacturer to fix the problem.
- Gather as much information as possible and escalate the problem.*
- Ask the customer to call again when another technician can provide a solution to the problem.
8. Which statement that is related to running 64-bit software is correct?
- 64-bit software requires a 64-bit processor but can run on a 32-bit operating system.
- 64-bit software requires a 64-bit processor and a 64-bit operating system.*
- 64-bit software can run on a 32-bit processor but requires a 64-bit operating system.
- 64-bit software can run on a 32-bit processor using a 32-bit operating system but the software performance will be slower.
9. Which statement is correct about installing a 32-bit operating system on a x64 architecture?
- The OS will always make use of all the RAM available.
- The OS will run correctly.*
- The OS can address more than 128 GB of memory.
- This combination will provide better security.
10. What action should a technician take before upgrading computers from Vista to Windows 7?
- Run Vista Upgrade Analyzer.
- Run Windows 7 Upgrade Advisor.*
- Uninstall all programs.
- Upgrade the video card.
11. What is a possible situation when it might be necessary to boot Windows 7 from a USB device, a CD, or a DVD?
- to disable background services
- to delete registry keys
- to partition the hard drive
- to repair the system*
12. What type of partition has the ability to create volumes spanning across more than one disk?
- primary
- active
- extended
- dynamic*
13. What type of file system allows the use of files larger than 5 GB and is mostly used on internal hard drives?
- FAT32
- FAT64
- NTFS*
- CDFS
- exFAT
14. Which user account should be used only to perform system management and not as the account for regular use?
- guest
- standard user
- administrator*
- power user
15. Which type of user account is created automatically during a Windows 8.1 installation?
- Administrator*
- Guest
- Remote Desktop user
- Standard user
16. A technician is attempting to repair a Windows 7 laptop that has a missing or corrupt OS file that prevents Windows 7 from starting up. The technician reboots the laptop and accesses the WinRE via the F8 key. Which option must the technician choose in the System Recovery menu to locate and fix the missing or corrupt system files?
- Startup Repair*
- System Restore
- System Image Recovery
- Windows Memory Diagnostic
17. When would the PXE option be used when repairing a PC?
- The display cannot be seen clearly.
- There is no response from the mouse or keyboard.
- The computer needs a replacement operating system.*
- A newly installed application caused the system to perform erratically.
18. A user wants to extend a primary partition formatted with the NTFS file system with the unallocated space on the hard disk. What must the user do after the primary partition is extended to make it usable?
- Convert the disk type to dynamic.*
- Ensure that the disk type is basic.
- Format the disk with the FAT64 file system.
- Partition the new space as a basic disk.
19. A user is viewing the Windows Disk Management utility and notices that one of the disks is marked as Foreign. What does this mean?
- This is a basic disk that has just been converted to a dynamic disk.
- This is a dynamic disk whose partition has been deleted.
- This is a dynamic disk from another PC running Windows.*
- This is a disk that does not contain a valid signature.
20. What are two file attributes in the Windows environment? (Choose two.)
- details
- archive*
- read-only*
- security
- general
21. What are two functions of hypervisors? (Choose two.)
- to partition the hard drive to run virtual machines
- to protect the host from malware infection from the virtual machines
- to manage virtual machines*
- to allocate physical system resources to virtual machines*
- to share the antivirus software across the virtual machines
22. Which Windows utility can be used to schedule a regular backup for preventive maintenance?
- Windows Task Scheduler*
- Windows Task Manager
- Disk Cleanup
- System Restore
23. Which statement is correct about applying firmware updates?
- Firmware updates are sometimes irreversible.*
- It is possible to use the Roll Back feature to reverse the change.
- The firmware updates can be installed automatically using the Windows Service Pack utility.
- Firmware updates should not be included as part of the preventive maintenance program.
24. What is true about restore points?
- Once System Restore is used to restore a system, the change is irreversible.
- Restore points back up personal data files.
- Restore points recover corrupted or deleted data files.
- Restore points should always be created before making changes to a system.*
25. A user has a computer that is infected with spyware. What should be performed before removing the spyware?
- Disable System Restore.*
- Run Windows Update.
- Run a disk defragmentation.
- Create a full backup.
26. A technician is troubleshooting a Windows 7 laptop that takes significantly longer than expected when performing a file search. What is the possible cause?
- The file system is corrupt.
- The disk type is basic.
- The disk type is dynamic.
- The file permissions are not set.
- The index service is not running.*
27. A user reports that a PC is losing files, not opening some files, and is performing slowly. The technician suspects problems with the hard drive. What should be done to protect the data that is on the PC and to determine the source of the problem, without risking total drive failure?
- Run the format command, then replace the hard drive.
- Run chkdsk, then run format.
- Back up all important files, then replace the hard drive.
- Back up all important files, then run chkdsk.*
- Run chkdsk, then back up all important files.
28. A user logs into Active Directory on a workstation and the user home directory does not redirect to a network share on a file server. A technician suspects that the group policy setting is incorrect. Which command can the technician use to verify the group policy settings?
- rstrui
- runas
- tasklist
- gpresult*
- gpupdate
29. A company has recently deployed Active Directory and now a workstation cannot connect to a network resource. A technician takes corrective action by modifying group policy settings. Which command should the technician use to make the workstation synchronize with the new settings?
- runas
- rstrui
- tasklist
- gpresult
- gpupdate*
30. A wired network is undergoing several changes that could leave it vulnerable to connection by unauthorized devices while the work is in progress. Which two temporary measures would enable the authorized devices to continue to have network access but prevent unauthorized devices from connecting? (Choose two.)
- Disable DNS.
- Disable SSID broadcast.
- Disable DHCP.*
- Subnet the network.
- Assign static IP addresses to the authorized devices.*
31. Refer to the exhibit. In what situation would a technician use this tab?
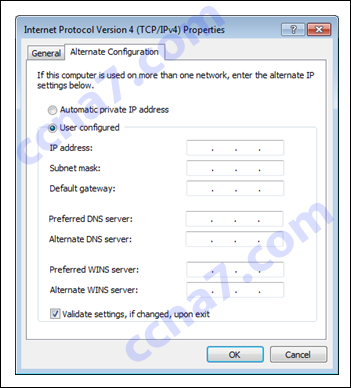
- When the device will not be using the Internet.
- When a laptop is used both at work with DHCP and at home with a static IP address.*
- When a device is behind a firewall and software is being used that needs access to a remote network.
- When the computer will be using a VPN connection and accessing the Internet while connected through the VPN.
32. On a PC that is running Windows 7 Ultimate, a user sets up a home entertainment system and creates a homegroup. The user then joins two other PCs to the workgroup, one PC running Windows 7 Starter and the other running Windows 7 Home Basic. What else must the user do in order to have the user accounts on the Windows 7 Home Basic and Windows 7 Starter PCs access the shares on the home entertainment system?
- Users have to be added to the user accounts on the home entertainment PC.
- Users on the PC that is running Windows Starter cannot join the homegroup.
- Users on the PC that is running Windows Home Basic will have to be manually added to the homegroup.
- User accounts on all three PCs have to be added to the homegroup.
- Nothing has to be done. All users accounts on all the PCs will automatically be added to the homegroup.*
33. A user is reporting that a file has been shared specifically with another user on the network, but the other user opens the file and is unable to save it once edited. What is the probable cause?
- The user shared the document with Read permissions.*
- The user forgot to share the parent folder.
- The file has the Archive attribute enabled.
- The file has been deleted.
34. Which character of the Cloud model provides easy monitoring, controlling, reporting, and billing for both the provider and customers?
- rapid elasticity
- resource pooling
- measured service*
- broad network access
- on-demand self-service
35. A business organization is configuring security on the mobile devices that are used in the organization. The security policy states that business data on mobile devices should only ever be accessed by employees. Which mobile device security feature can be used to best ensure that business data is rendered completely inaccessible if the device is lost or stolen?
- remote lock
- remote wipe*
- passcode lock
- sandbox
36. An administrative assistant tries to link a Bluetooth keyboard and mouse to a computer. The keyboard does not work, but the mouse works fine. What are two issues that could cause this situation? (Choose two.)
- Wi-Fi is turned off.
- The keyboard battery is dead.*
- Bluetooth is turned off.
- The Num Lock key has been inadvertently pressed.
- The keyboard is too far from the computer.*
37. What is needed from Apple and Google in order for individual programmers to develop apps for iOS and Android devices?
- SLA
- SDK*
- firmware
- iOS or Android device
38. Which type of malware is disguised as a legitimate program?
- adware
- worm
- Trojan*
- spyware
39. After complaints from users, a technician identifies that the college web server is running very slowly. A check of the server reveals that there are an unusually large number of TCP requests coming from multiple locations on the Internet. What is the source of the problem?
- A DDoS attack is in progress.*
- The server is infected with a virus.
- There is insufficient bandwidth to connect to the server.
- There is a replay attack in progress.
40. Which security threat hides the resources that it uses from antivirus programs?
- worm
- Trojan
- rootkit*
- spyware
41. A user receives an email requesting verification of the password that is used to access bank files. What type of security threat is this?
- virus
- social engineering
- phishing*
- malware
42. A cleaner attempts to enter a computer lab but is denied entry by the receptionist because there is no scheduled cleaning for that day. What type of attack was just prevented?
- Trojan
- shoulder surfing
- war driving
- social engineering*
- phishing
43. Which two precautions can help prevent social engineering? (Choose two.)
- Always ask for the ID of unknown persons.*
- Escort all visitors.*
- Keep your password securely under your keyboard.
- Do not allow any customers into the workplace.
- Always require a user name and password to be configured.
44. A company has replaced five desktop computers in the accounting and finance department with new computers. The plan is to donate the recovered computers in a fully functional state to a not-for-profit community organization. How can the company ensure that sensitive financial data cannot be accessed once the computers are donated?
- Data wipe the hard drives by using specialized software.*
- Perform a high-level format on the hard drives.
- Drill holes through the hard drive platters.
- Delete all the files and directories on the hard drives.
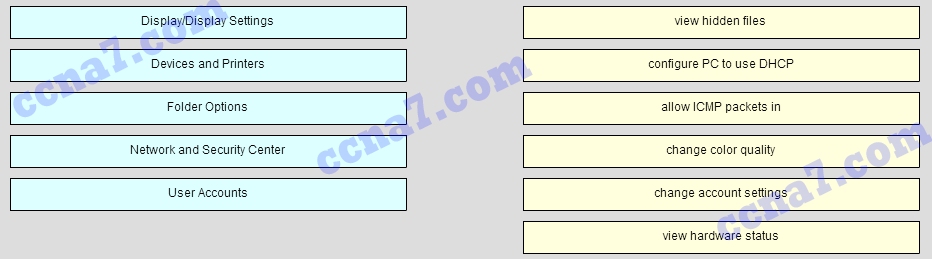
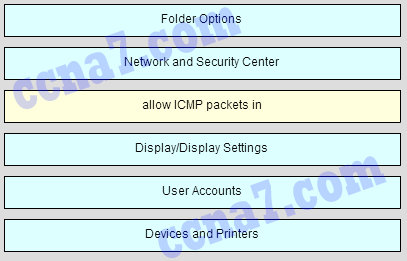
45. Match the task to the Windows Control Panel utility. (Not all options are used.)
Question
Answer
EmoticonEmoticon